Does “ThingBot” excist? [----> Read More]
Blog about the latest in Mobile Commerce, Mobile Devices, Mobile Security and Social Media.
Friday, January 31, 2014
Internet of Things: BotNets exist. ThingBots do not
Thursday, January 30, 2014
How To Protect Your Smartphone or Tablet in 2014
until 2011 PC's and Laptops where mainly targeted by virusses. Until then Mobile devices have flown under the threat radar with PCs mainly taking the abuse. As a result, many smartphone and tablet owners give little thought to the risks that lurk behind deceivingly harmless apps.
It's not a surprise that smartphones and tablets are no safer from invasions than computers. A digital device is a digital device, regardless of its size and portability. Nonetheless there are a number of ways you can protect your phone or tablet (DO) and there are a number of things you should be aware (DON'T) which I will list below:
READ MORE: HERE
READ MORE: HERE
Wednesday, January 29, 2014
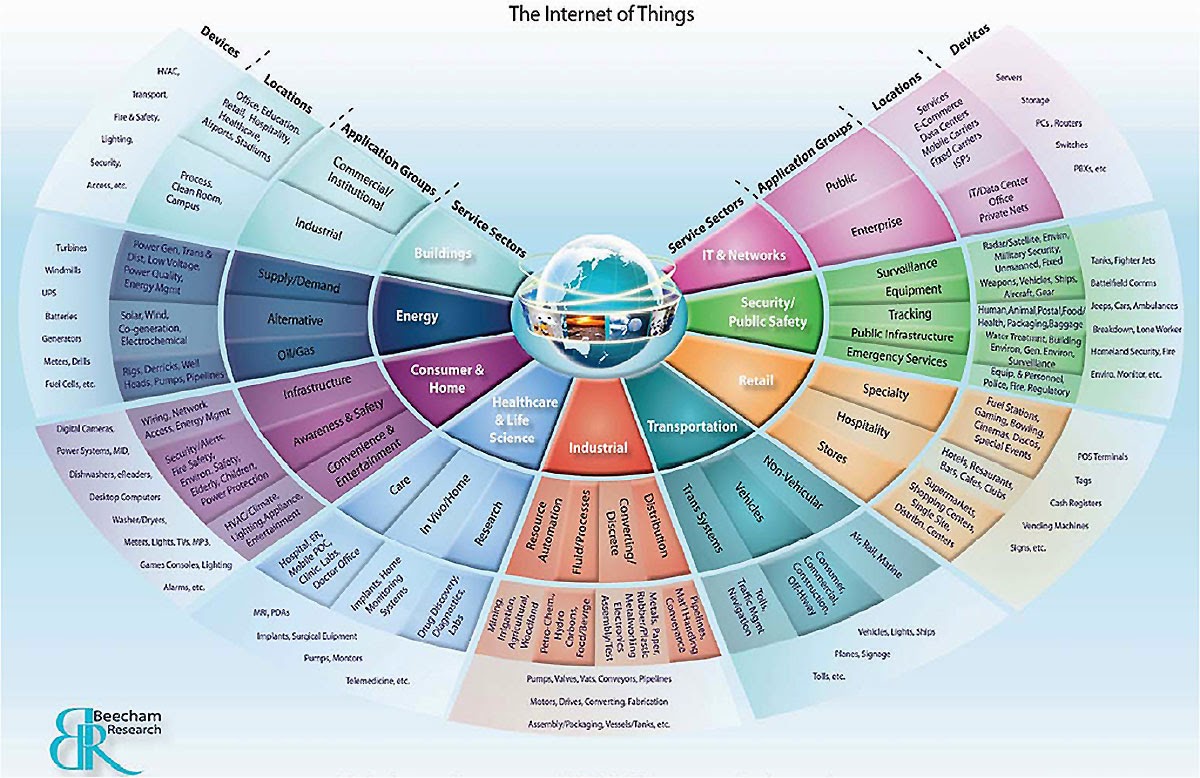
The Internet of Things: Top 5 Device Security Tips VISIT
blog courtesy of www.insidedevices.org
Gates’ could control about anything in his house by the tap of his finger, whilst driving his car 20 miles away from his house.
Welcome to the “The Internet of Things“(IoT) that does represent a revolution happening right now. All kind of companies – not just technology and telecommunications firms – are linking “things” as diverse as smartphones, cars and household appliances to industrial-strength sensors, each other and the internet. The technical result may be simple features such as intercommunication and autonomous machine-to-machine (M2M) data transfer, but the potential benefits to lifestyles and businesses are unprecedented.
Ofcourse there is a “But”….with great opportunity comes great responsibility. Along with its conveniences, the IoT will be exposed to unprecedented security challenges: data privacy, safety, governance and trust.
What Are The Main Security Loopholes?
Security loopholes can occur anywhere in the IoT; but you can devide into two groups:
Data Risks: all smart devices will transmit data to a storage point before (in most cases) a bulk upload to the provider, often with outdate security settings.
Privacy Risks: all our smart devices collect, aggregate and transmit our user data, even tiny items of data in aggregate can identify, define, and label you without your knowledge.
What Can You Do To Protect Your Data and Privacy?
- Audit the devices you own.
- Secure your device. If a device is connected to your network, it means that it is potentially accessible over the internet.
- Verify the security settings on any device you purchase. If it is remotely accessible, disable this feature if it isn’t required
- Change any default passwords to something only you know. A long combination of letters, numbers and symbols will generate a strong password.
- Check the manufacturer’s website to see if there are updates to the device’s software. If security vulnerabilities are discovered, manufacturers will often patch them in new updates to the software. PATCHING IS EVERYTHING
What Is The Best Example Day-To-Day Example of A Device That Poses A Risk To Our Data and Privacy?
Read the full article here
Subscribe to:
Posts (Atom)