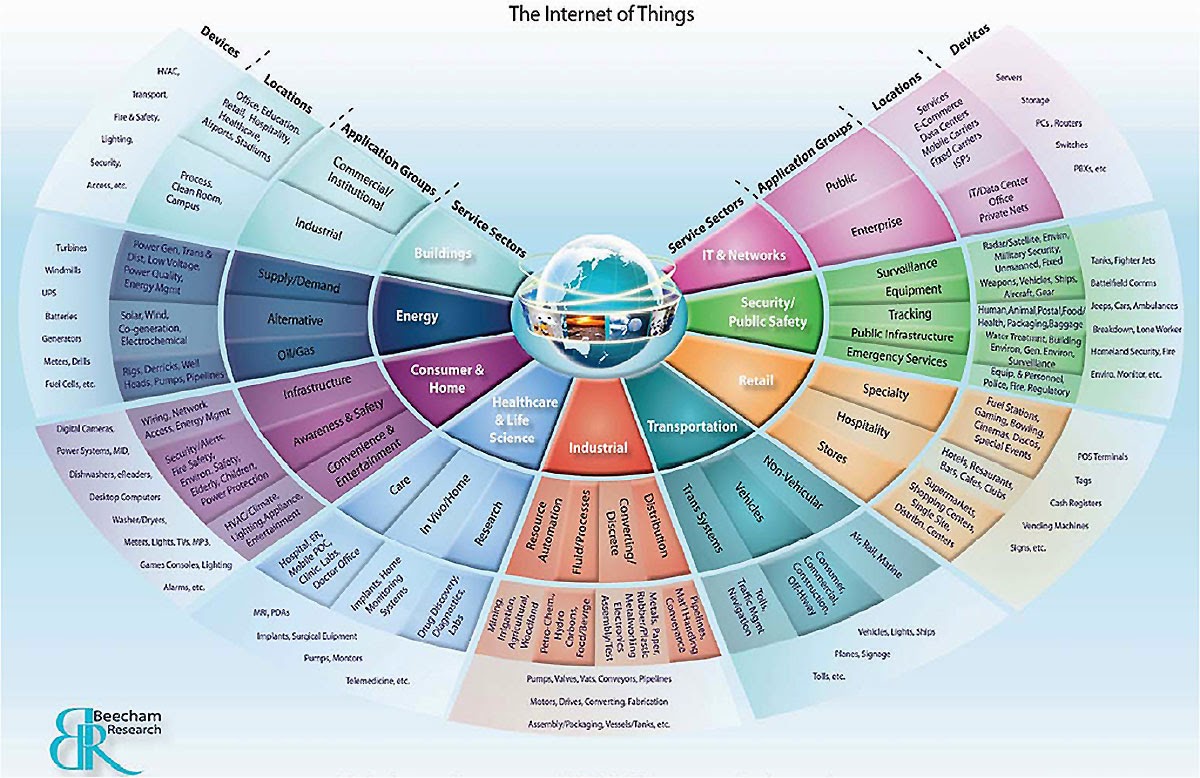
On the 16th of January 2014 Proofpoint (Leading Security Firm) claims to have uncovered what could be the first proven Internet of Things (IoT)-based cyberattack involving conventional household “smart” appliances. The global attack campaign involved more than 750,000 malicious email communications coming from more than 100,000 everyday consumer gadgets such as home-networking routers, connected multi-media centers, televisions and at least one refrigerator (What? A FRIDGE!) that had been compromised and used as a platform to launch attacks.
On the 16th of January 2014 Proofpoint (Leading Security Firm) claims to have uncovered what could be the first proven Internet of Things (IoT)-based cyberattack involving conventional household “smart” appliances. The global attack campaign involved more than 750,000 malicious email communications coming from more than 100,000 everyday consumer gadgets such as home-networking routers, connected multi-media centers, televisions and at least one refrigerator (What? A FRIDGE!) that had been compromised and used as a platform to launch attacks.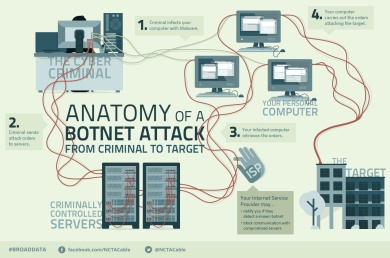 Just as personal computers can be unknowingly compromised to form robot-like “botnets” that can be used to launch large-scale cyberattacks, Proofpoint’s findings alledge that cyber criminals have begun to commandeer home routers, smart appliances and other components of the Internet of Things and transform them into “thingbots” to carry out the same type of malicious activity. Cyber criminals intent on stealing individual identities and infiltrating enterprise IT systems have found a target-rich environment in these poorly protected internet connected devices that may be more attractive and easier to infect and control than PC, laptops, or tablets.
Just as personal computers can be unknowingly compromised to form robot-like “botnets” that can be used to launch large-scale cyberattacks, Proofpoint’s findings alledge that cyber criminals have begun to commandeer home routers, smart appliances and other components of the Internet of Things and transform them into “thingbots” to carry out the same type of malicious activity. Cyber criminals intent on stealing individual identities and infiltrating enterprise IT systems have found a target-rich environment in these poorly protected internet connected devices that may be more attractive and easier to infect and control than PC, laptops, or tablets.
Does “ThingBot” excist? [----> Read More]