After my last blog I started to brainstorm about the level and what type of security risks M-Commerce and Social Commerce need to mitigate or assure. Given the rise of sales in Smartphones and Tablets and the immense volume of downloadable applications and increasing volume of apps being developed, (personal) data and the protection of it will be key for any business to succeed.
In this blog I will provide a bit more background on the type of security issues M-Commerce & M-Users are exposed.
Furthermore I will try to provide some information on who are what creates those threats and what the key drivers are. To finalize a current overview of the business practices and which security gaps need to be closed fast.
"We saw mobile malware grow from zero to 350,000 in three years, while in the PC world, it took 14 years to reach that number," Trend Micro CTO Raimund Genes.
The current situation, signaled by the US Federal Trade Commission (FTC) this month and echoed by leading mobile security providers like Metaforic and Infosecurity, creates a catastrophic risk to individuals, businesses and governments
The FTC & leading industry security providers base their outcry on two missing key components:
- Lack of standards and wide variety of development practices
- Low awareness of security risks by consumers
"FTC officials are likening the current state of the country’s mobile security practices to the “wild, wild west,” suggesting that many companies operating in the mobile space have little to no concern for mobile security" source John Torney
According to new research (Nov. 2012 by Bit9) one-quarter of more than 400.000 Android Apps examined in the Google's Play store pose security risks to mobile-device users.
Bit9 notes this doesn't means these apps are Malware, but they could do damage if compromised because the user granted (so much) permission. These are POTENTIAL threats!!
Bit9 categorized these "questionable" and "suspicious" Android Apps in Google Play as follows:
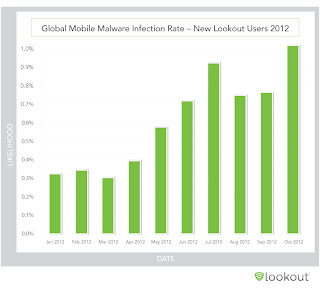
The Global Likelihood that a new user encountered a mobile threat from June '12 till October '12 was 0,84%
The statistic seems relatively small, however the volume of current mobile device users, but keep in mind that every threat is driven by financial, political and/or publicity motivations
Most people including myself think of cyber crime as so fat hacker trying to steal money from you. Truth is that any kind of Malware developed is designed to directly obtain your personal data and to distribute it for financial, political or publicity gain.
Political gain probably will raise an eyebrow with a lot of people since in the Western world this is somewhat outdated (except for Richard Nixon in the 70's). During the last Russian General Elections various cyber attacks aimed at opposition parties did take its tolls with servers being offline at times it needed to be online, effectively depriving parties to broadcast and interact with the public.
2013 Predictions
Toll Fraud Takes the Cake in 2013
Toll fraud will continue to dominate the 2013 mobile threat space, despite forward momentum on the platform to block these types of attacks. This is due to the following:
The 2013 outlook presents a complex challenge as supply and demand both from business and mobile device users is increasing, so is the availability and implementation of new technologies and innovations.
The thin line between data security and data breach is only a push of a button away....
This is the end of part I of this blog! Thank you for reading! In my next blog I will go further into Toll Fraud and other security threats to our mobile devices and mobile businesses!
Want to know a bit more? Download Verizon's Data Breach Verification Report by pushing the button
In this blog I will provide a bit more background on the type of security issues M-Commerce & M-Users are exposed.
Furthermore I will try to provide some information on who are what creates those threats and what the key drivers are. To finalize a current overview of the business practices and which security gaps need to be closed fast.
"We saw mobile malware grow from zero to 350,000 in three years, while in the PC world, it took 14 years to reach that number," Trend Micro CTO Raimund Genes.
The FTC & leading industry security providers base their outcry on two missing key components:
- Lack of standards and wide variety of development practices
- Low awareness of security risks by consumers
"FTC officials are likening the current state of the country’s mobile security practices to the “wild, wild west,” suggesting that many companies operating in the mobile space have little to no concern for mobile security" source John Torney
According to new research (Nov. 2012 by Bit9) one-quarter of more than 400.000 Android Apps examined in the Google's Play store pose security risks to mobile-device users.
Bit9 notes this doesn't means these apps are Malware, but they could do damage if compromised because the user granted (so much) permission. These are POTENTIAL threats!!
Bit9 categorized these "questionable" and "suspicious" Android Apps in Google Play as follows:
- 42% access GPS location data (incl. wallpapers, games & utilities)
- 31% access phone calls or phone numbers
- 26% access personal data (contacts + emails)
- 9% use permissions that can cost the user money
Bit9 defined risk level according to relative degrees of privacy intrusion and the App's feature set (f.i. ability to wipe devices or change system settings)
More interesting are the findings of a survey of 138 IT professionals responsible for the mobile security of over 400.000 users (employees) in their organizations.
- 78% don't believe mobile manufactures focus enough on security
- 71% allow employee owned devices to access their organizations network
- 93% allow Apple's IOS to access their organizations network
- 77% allow Android devices to access their organizations network
- 96% allowing personal devices also allow employees to access email using the device
- 85% allow personal devices to access the company calendar data
In 2013 people will purchase more than 1,2 billion mobile devices. Mobile platforms will continue to expand at rocket speed, as people are forecast to download over 70 billion mobile apps by 2014
Some recent examples of corporate data breaches
Some recent examples of corporate data breaches
- Jan. 21. Human Resources and Skills Canada bans use of portable data devices following a data breach affecting 583,000 persons. The breach resulted from a hard drive discovered missing since November 2012. The disk contained names, birth dates, addresses, social insurance numbers and student loan balances for persons with loans through the Canada Student Loan Program from 2000 to 2006.
- Jan 23. Lucile Packard Children's Hospital in Palo Alto, Calif., and the Stanford University School of Medicine reveal they're notifying about 57,000 patients about a data breach that occurred Jan. 9. The breach happened when a password-protected laptop was stolen from a physician's car.
- Jan 24. Jeffrey Ness, one of 5000 people affected by unauthorized access to motor vehicle records by a Minnesota state employee, files lawsuit in federal district court alleging violation of data privacy laws.
- Jan. 24. Sony Computer Entertainment Europe is fined $395,000 by the UK's Information Commissioners Office for a data breach in April 2011 that compromised information -- including credit card numbers -- for millions of customers
2013 Likelihood of Encountering a Threat
The Global Likelihood that a new user encountered a mobile threat from June '12 till October '12 was 0,84%
The statistic seems relatively small, however the volume of current mobile device users, but keep in mind that every threat is driven by financial, political and/or publicity motivations
Most people including myself think of cyber crime as so fat hacker trying to steal money from you. Truth is that any kind of Malware developed is designed to directly obtain your personal data and to distribute it for financial, political or publicity gain.
Political gain probably will raise an eyebrow with a lot of people since in the Western world this is somewhat outdated (except for Richard Nixon in the 70's). During the last Russian General Elections various cyber attacks aimed at opposition parties did take its tolls with servers being offline at times it needed to be online, effectively depriving parties to broadcast and interact with the public.
2013 Predictions
Toll Fraud Takes the Cake in 2013
Toll fraud will continue to dominate the 2013 mobile threat space, despite forward momentum on the platform to block these types of attacks. This is due to the following:
- Systems Architecture: Premium SMS protections are only baked into the latest versions of Android (4.2 / Jelly Bean); the first devices are just now shipping with this firmware version, and will not significantly penetrate the market until late 2013.
- Ease of Attack: Toll fraud will remain the easiest path to financial gain for malware authors within the base of mobile consumers. It does not require significant technical sophistication and provides considerable "easy money" that is built into most mobile networks via pre-existing billing channels. A 2012 example, FakeInst, pretended to act as an installer for legitimate popular apps such as the Opera Browser (hence the names ‘OpFake’ and ‘Fakebrows’) or WhatsApp Messenger.
Spam Heats Up on Mobile
SMS-based spam will increase in its volume across mobile networks in 2013. A surge in the number of malicious applications, toll fraud-based and otherwise, such as ConnectSMS, actively collecting contact information from infected devices.
Mobile Banking/Payments Top of Mind But Have Little Payoff
Mobile banking has become mainstream, and mobile bank fraud has continued to remain an issue, predominately for European users. The majority of mobile banking threats begin with PC-based malware and include a malicious mobile app that intercepts verification codes, known as mTANs, sent to customers’ devices via SMS. Standalone mobile banking fraud without a PC component is not yet prevalent. Mobile payments are still in their early stages;
Mobile Becomes Hotspot for Targeted Political Surveillance
In 2012, FinSpy provided the first evidence that mobile surveillanceware is actively being used to monitor political targets. Marketed to law enforcement personnel, FinSpy software was discovered targeting human rights activists in Bahrain. We expect to find more politically motivated targeted surveillanceware emerge in 2013.
Businesses Challenged with Employee Empowerment vs. Control
Finding the right balance between protection and employee empowerment will be the challenge of 2013. Over the past few years, there has been a surge in the Bring Your Own Device (BYOD) phenomenon. Employees often use consumer cloud services to store / transfer sensitive corporate information, broadening the target, often accessing these at work, or Bring Your Own Network (BYON). As corporate IT administrators seek to gain control over mobile devices, there is potential that by over-correcting for the problem, employees will seek new ways to subvert processes and policies that constrain the pure consumer experience.
Mobile App & Browser – Constant Threat Vectors
Mobile applications will remain the central collection point for our personal data – from location information, messaging, calendars to social circles. They will also remain the most straightforward channel for privacy attacks that seek to collect that data. The mobile browser will continue to be the largest remote attack surface on mobile devices. Attacks of this type provide a vector for intruders to attempt to break in, independent of creating a trojanized mobile application, making it a target for a broad-based attack.
Privacy Crackdowns Happen Across the Board
Mobile privacy will be a major issue in 2013, as long as applications continue to access personal or device-specific information without gaining proper informed consent. There will be continued pressure on app developers in the form of government action, industry self-regulation and consumer pressure. The State of California has started to crackdown on apps and developers that do not provide sufficient mobile privacy policies.
The 2013 outlook presents a complex challenge as supply and demand both from business and mobile device users is increasing, so is the availability and implementation of new technologies and innovations.
The thin line between data security and data breach is only a push of a button away....
This is the end of part I of this blog! Thank you for reading! In my next blog I will go further into Toll Fraud and other security threats to our mobile devices and mobile businesses!
Want to know a bit more? Download Verizon's Data Breach Verification Report by pushing the button




No comments:
Post a Comment